A new ransomware called “Locky” is circulating via email. It comes in as a message with an invoice.doc attachment. If you open the attachment and don’t block macros from temporary locations in Word, the macro will run and start encrypting your Office and PDF files.
Fortunately, your junk filter may catch some of these files. Here is what mine looked like this morning.

Locky ransomware junk emails
When you check your own Junk folder for legitimate emails, don’t make the mistake of thinking these are legit. The sender name and email will probably be from someone you don’t recognize.
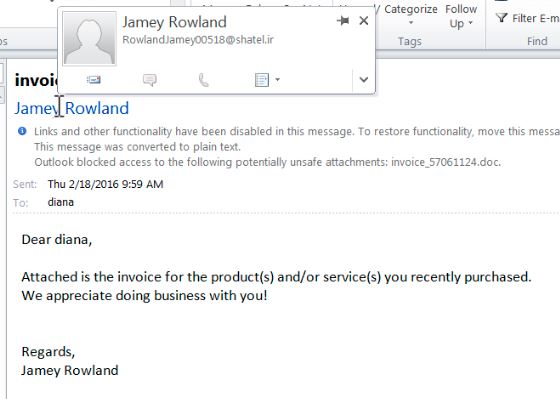
Locky ransomware email from unknown user
No anti-virus or anti-malware program can fully protect your computer from infection because new malware is written every day. The only way to be 100% safe is to disconnect your computer from the Internet and avoid attaching any external devices. But those precautions make your computer useless.
The second best safeguard is YOU. A little common sense goes a long way in dealing with email scams like this one.
- If you don’t know the sender, don’t open the email.
- If you aren’t involved in purchasing under your email, no one should be sending you an invoice anyway.
- Most invoice attachments would be PDF files, not DOC.
Any legitimate email with an invoice attachment should include all of the following criteria:
- Your own expectation of said email because you made a purchase or know that someone in your firm or household made a purchase and you are listed as the billing contact
- An email domain from a known vendor
- A subject line or message text explaining that an invoice is attached and what it’s for (e.g., a specified project, time period, or account number)
This post is aimed at prevention, rather than repair. However, if you received a suspicious invoice email and opened it, try scanning your PC with Microsoft Security Essentials to remove Locky. You can also try recovering your computer to a previous good restore point using System Restore. After removing the virus, recheck for encrypted files, which will have a .locky extension. Those files will have to be restored from backup if System Restore doesn’t recover them. Google “Locky ransomware” for additional information.








Leave a Reply