Last night, BeepingComputer.com posted this article, Vaccine, not Killswitch, Found for Petya (NotPetya) Ransomware Outbreak, detailing how to protect against the latest ransomware infecting computers throughout Europe and abroad. White hat hackers have reviewed the Petya code and determined that it’s looking for a file called Perfc. Once Petya (at least the current strain) encounters the file, it immediately stops the infection. You can easily create a read-only file in C:Windows using Notepad.exe. The folks at Bleeping Computer provide screen captures and instructions showing you exacting how to do that.
Faster Option – Batch File
A faster option is to run a batch file created by Lawrence Abrams which we have reviewed and run ourselves, and uploaded to our servers: https://sacomedia.com/downloads/nopetyavac.bat. A .bat file is an executable file, meaning it will run something. Batch files run a string of simple commands. If your anti-virus software won’t let you download a .bat file, you can copy and paste the batch code into a text editor like Notepad.exe and name it anything you want with a .bat file extension. Here is what is in the batch file:
@echo off
REM Administrative check from here: https://stackoverflow.com/questions/4051883/batch-script-how-to-check-for-admin-rights
REM Vaccination discovered by twitter.com/0xAmit/status/879778335286452224
REM Batch file created by Lawrence Abrams of BleepingComputer.com. @bleepincomputer @lawrenceabrams
echo Administrative permissions required. Detecting permissions...
echo.
net session >nul 2>&1
if %errorLevel% == 0 (
if exist C:Windowsperfc (
echo Computer already vaccinated for NotPetya/Petya/Petna/SortaPetya.
echo.
) else (
echo This is a NotPetya/Petya/Petna/SortaPetya Vaccination file. Do not remove as it protects you from being encrypted by Petya. > C:Windowsperfc
echo This is a NotPetya/Petya/Petna/SortaPetya Vaccination file. Do not remove as it protects you from being encrypted by Petya. > C:Windowsperfc.dll
echo This is a NotPetya/Petya/Petna/SortaPetya Vaccination file. Do not remove as it protects you from being encrypted by Petya. > C:Windowsperfc.dat
attrib +R C:Windowsperfc
attrib +R C:Windowsperfc.dll
attrib +R C:Windowsperfc.dat
echo Computer vaccinated for current version of NotPetya/Petya/Petna/SortaPetya.
echo.
)
) else (
echo Failure: You must run this batch file as Administrator.
)
pause
Websites can be hacked, even our SSL/TLS encrypted website. So, always check to see what’s in a batch file BEFORE YOU RUN IT by opening it in Notepad.exe and reading what the file does. Lawrence’s batch checks to see if you already have a Perfc file in C:Windows (“if exist C:Windowsperfc…”). The batch file then tells you what it is doing by outputting messages to your computer screen (“echo”). It then creates Perfc, Perfc.dat and Perfc.dll files (the three versions identified as files the ransomware looks for as an off switch). These Perfc files have nothing in them except a warning not to delete the files from Windows. The final part of the batch file makes the Perfc files read only (“attrib +R”). This batch file is simple and basic and doesn’t do anything weird. But if you don’t want to download the batch file from the link above, you can follow Bleeping Computer’s instructions for manually creating the files (link at the top) or you can simply copy the text for the batch file into a Notepad file and call it, for example, “vaccine.bat.” The “.bat” file extension is essential. You can save that file to your download directory or desktop. Once that’s done, just run the file as an administrator and follow the single prompt to “continue.”
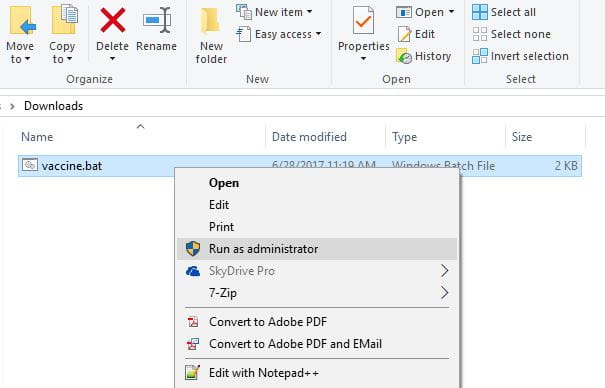
How To Run a File as Administrator
Even if you have user administrator rights on your PC, Windows doesn’t always let you run files as an administrator. To run this as an admin, just right-click on the file and select “Run as administrator.”
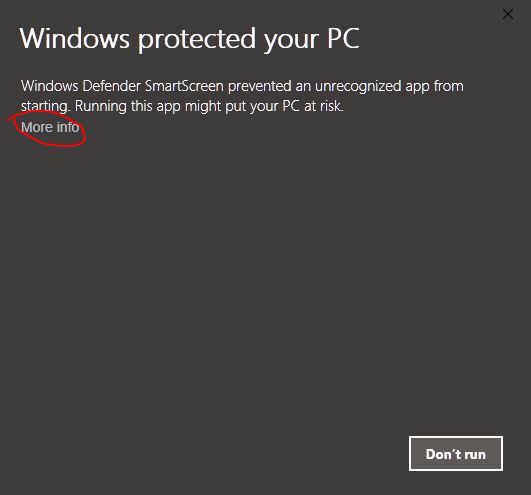
Windows Protecting You Against Yourself
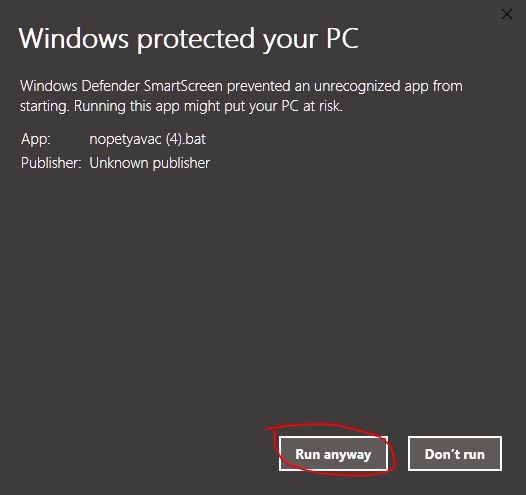
If the Windows Protected popup still blocks you from running the batch file, click on “More info.”
Best Prevention (for Mac User Too, Just in Case)
One of the most important components of hacking is the “social engineering attack.” It relies on human psychology to understand how to get people to click on something they shouldn’t. Email attachments are the easiest trigger. Use extreme caution before clicking any email attachment, even from people you know. If you aren’t expecting a file attachment, contact the person who sent it and confirm he or she sent it before you click the attachment.
The Bottom Line
Just run this batch file as an administrator to protect against the current strain of Petya ransomware: https://sacomedia.com/downloads/nopetyavac.bat. Also, run Windows Update to give Microsoft a chance to patch this and other vulnerabilities.








Leave a Reply